Weekly Update 297
Troy Hunt
MAY 28, 2022
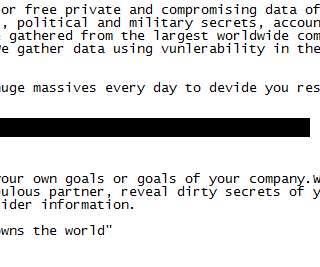
So I basically spent my whole day yesterday playing with Ubiquiti gear and live-tweeting the experience 😊 This was an unapologetically geeky pleasure and it pretty much dominates this week's video but hey, it's a fun topic. Still, there's a bunch of data breach stuff up front and as I write this, 25M more records courtesy of the MGM breach are making their way up into HIBP.


























Let's personalize your content