New Windows Subsystem for Linux malware steals browser auth cookies
Bleeping Computer
MAY 28, 2022
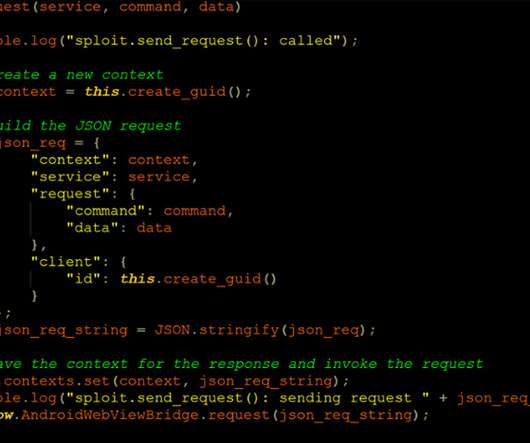
Hackers are showing an increased interest in the Windows Subsystem for Linux (WSL) as an attack surface as they build new malware, the more advanced samples being suitable for espionage and downloading additional malicious modules. [.].

























Let's personalize your content