Cyberwar: The smart person's guide
Tech Republic Security
MAY 16, 2016
Armies around the world are gearing up for cyberwarfare: here's what it is and what you need to know.

Tech Republic Security
MAY 16, 2016
Armies around the world are gearing up for cyberwarfare: here's what it is and what you need to know.
NopSec
MAY 17, 2016
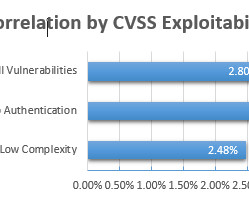
Note: This article was updated in June 2022. Here at NopSec, we are all about risk — our number one goal as a company to help organizations evaluate and reduce their risk. However, the term “risk” can be highly subjective, making it difficult for organizations to determine the riskiest vulnerabilities. One quantitative measure NopSec employs to help an organization evaluate the risk of a vulnerability is through malware correlation.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MAY 17, 2016
Experts offer five scenarios they suspect will wreak havoc on cybersecurity by 2020.

Tech Republic Security
MAY 16, 2016
HPE's new Business of Hacking report takes a look at the underground world of criminal hackers and what steps businesses can take to stay secure.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
MAY 19, 2016
Read about the potential devastating effects of business ID theft, and what steps experts are taking to address this issue.

Tech Republic Security
MAY 16, 2016
If you're serious about security on your Linux machines, you might want to clear the bash history. Learn how to do this more effectively than with just a single command.
Let's personalize your content