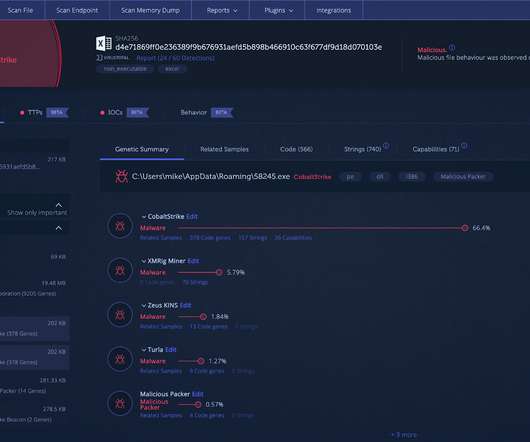
How Cobalt Strike Became a Favorite Tool of Hackers
eSecurity Planet
MARCH 14, 2022
Pentesting involves vulnerability exploitation and post-exploitation actions – the idea is to conduct a real attack, like cybercriminals would do, except with an explicit authorization from the company in order to identify weaknesses and improve security defenses. While that’s true, it requires time, effort, and energy.










Let's personalize your content