Russia-linked Nobelium APT targets orgs in the global IT supply chain
Security Affairs
OCTOBER 25, 2021
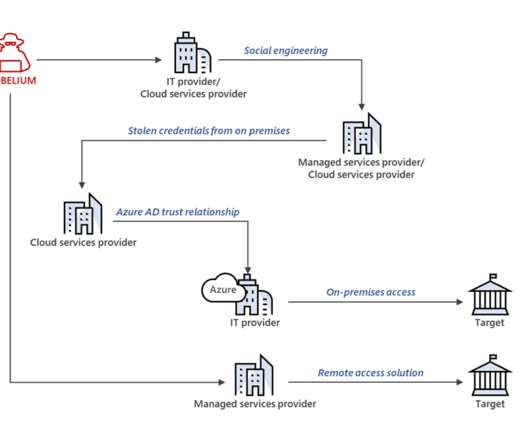
NOBELIUM focuses on government organizations, non-government organizations (NGOs), think tanks, military, IT service providers, health technology and research, and telecommunications providers. ” states Microsoft.










Let's personalize your content