Hacking Wireless Bicycle Shifters
Schneier on Security
AUGUST 20, 2024
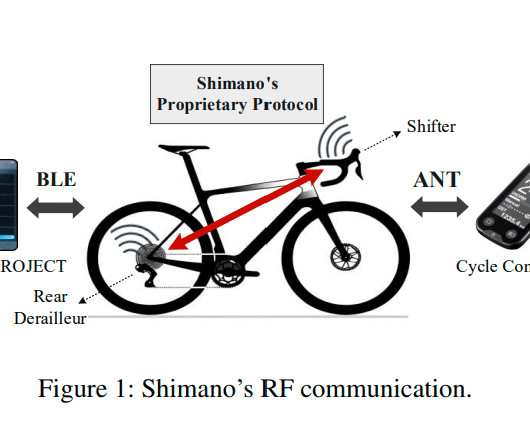
This is yet another insecure Internet-of-things story , this one about wireless gear shifters for bicycles. These gear shifters are used in big-money professional bicycle races like the Tour de France, which provides an incentive to actually implement this attack. Research paper. Another news story. Slashdot thread.


















Let's personalize your content