City of Dallas has set a budget of $8.5 million to mitigate the May Royal ransomware attack
Security Affairs
SEPTEMBER 23, 2023
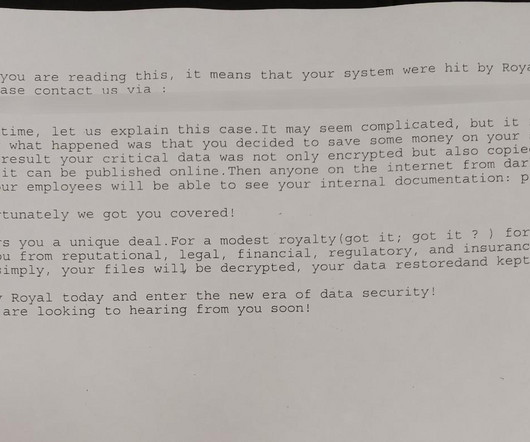
The City experts believe that the group specifically targeted a prioritized list of servers using legitimate Microsoft system administrative tools. Early on the morning of Wednesday, May 03, 2023, the group started executing the ransomware on the City of Dallas. The Dallas City Council has approved a budget of $8.5














Let's personalize your content