How to Write a Pentesting Report – With Checklist
eSecurity Planet
OCTOBER 31, 2023
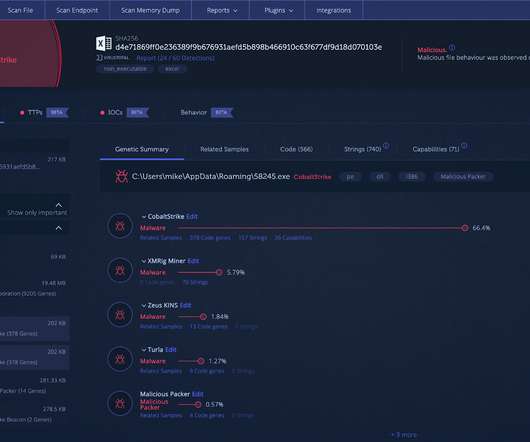
A penetration testing report discloses the vulnerabilities discovered during a penetration test to the client. Penetration test reports deliver the only tangible evidence of the pentest process and must deliver value for a broad range of readers and purposes.


















Let's personalize your content