Using Threat Modeling to Boost Your Incident Response Strategy
The State of Security
AUGUST 22, 2021
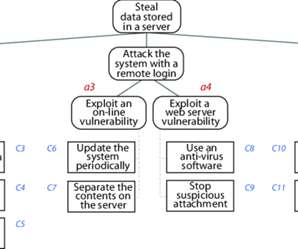
Threat modeling is increasing in importance as a way to plan security in advance. Instead of merely reacting to threats and incidents, an organization can identify and evaluate its security posture, relevant threats, and gaps in defenses that may allow attacks to succeed.


















Let's personalize your content