Leverage Threat Intelligence, AI, and Data at Scale to Boost Cyber Defenses
Dark Reading
JULY 19, 2023
By combining these leading-edge tools, security professionals can amplify the impact of their security strategies.

 threat-intelligence leverage-threat-intelligence-ai-and-data-at-scale-to-boost-cyber-defenses
threat-intelligence leverage-threat-intelligence-ai-and-data-at-scale-to-boost-cyber-defenses 
Dark Reading
JULY 19, 2023
By combining these leading-edge tools, security professionals can amplify the impact of their security strategies.

eSecurity Planet
DECEMBER 19, 2023
We each need to consider how these trends may affect our organizations and allocate our budgets and resources accordingly: AI will turbo-charge cybersecurity and cyberthreats: Artificial intelligence (AI) will boost both attackers and defenders while causing governance issues and learning pains.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
MAY 24, 2023
A cloud workload protection platform (CWPP) shields cloud workloads from a range of threats like malware, ransomware, DDoS attacks, cloud misconfigurations, insider threats, and data breaches. per server per month. per server per month.
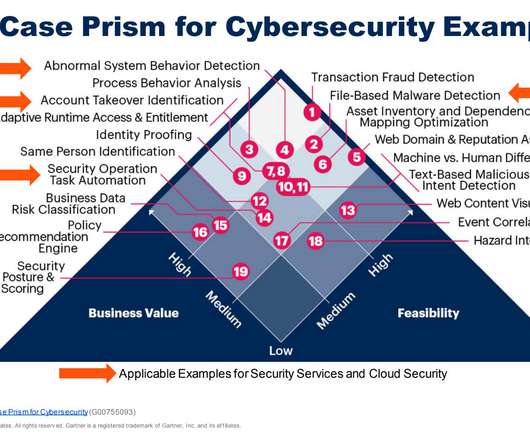
eSecurity Planet
JUNE 22, 2022
Next-gen AI systems are now baked into just about every category of software—but Gartner believes we can automate even further. And in cybersecurity, hyperautomation could be the thing that makes the constant onslaught of alerts and cyber incidents manageable. See the Top MDR Services and Solutions. What is Hyperautomation?

eSecurity Planet
AUGUST 10, 2023
Top CSPM Solutions Bottom Line: Boost Cloud Security with CSPM How Does Cloud Security Posture Management (CSPM) Work? CSPM tools can discover issues like missing encryption on data, databases or storage; excessive account privileges; exposed data; misconfigured connections; and missing or misconfigured security controls.

Cisco Security
AUGUST 26, 2021
We constantly see new threats, and threat vectors, come and go; which puts a tremendous strain on the InfoSec teams that have to protect organizations and businesses from these threats. Cybersecurity is a continuously evolving landscape. We here in the Cisco Secure Technical Alliance (CSTA) live by that principle.
Let's personalize your content