Onapsis and SAP Partner to Secure Business
Security Boulevard
APRIL 28, 2022
Onapsis and SAP Partner to Secure Business. Onapsis was founded over a decade ago when we realized that the world’s most critical enterprise resources were being overlooked. nd vulnerabilities present in systems even though SAP released patches years ago. maaya.alagappan. Thu, 04/28/2022 - 14:39. Meet us there!




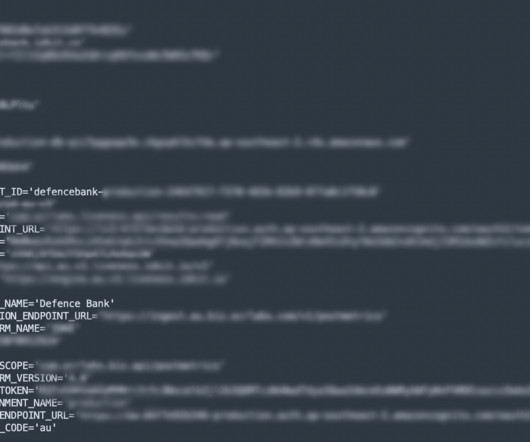



















Let's personalize your content