A million at risk from user data leak at Korean beauty platform PowderRoom
Security Affairs
MARCH 23, 2023
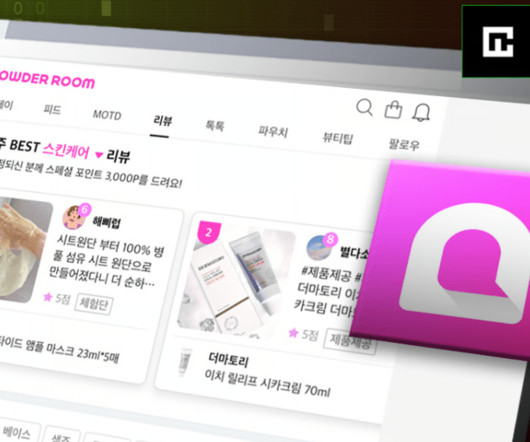
South Korean beauty content platform, PowderRoom, has leaked the personal information of nearly one million people. Established in 2003, PowderRoom is a South Korean beauty content platform connecting 3.5 Among the leaked data, researchers found a million tokens used for authentication and accessing the website.












Let's personalize your content