Mandiant identifies 3 hacktivist groups working in support of Russia
Security Affairs
SEPTEMBER 27, 2022
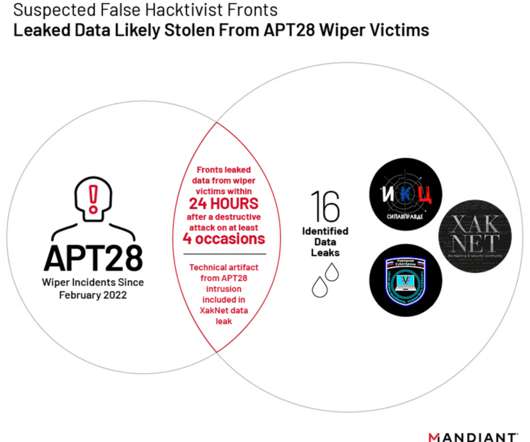
The so-called hacktivist groups conducted distributed denial-of-service (DDoS) and defacement attacks against Ukrainian websites, but the experts believe that they are a front for information operations and destructive cyber activities coordinated by the Kremlin. Most of APT28s’ campaigns leveraged spear-phishing and malware-based attacks.
















Let's personalize your content