Lazarus group uses fake cryptocurrency apps to plant AppleJeus malware
Malwarebytes
DECEMBER 5, 2022
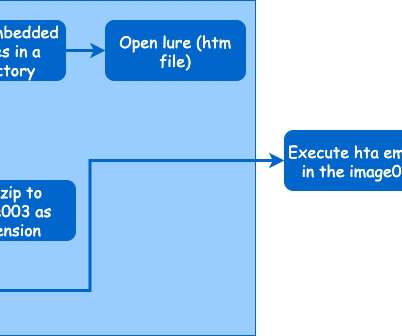
It's been active since 2009 and is responsible for many high profile attacks. In January of 2022 the Malwarebytes Intelligence Team uncovered a campaign where Lazarus conducted spear phishing attacks weaponized with malicious documents that used a familiar job opportunities theme. Lazarus Group. The new campaign. Second wave.










Let's personalize your content