How To Protect Against A Phishing Attack And How To Counter Them
SiteLock
AUGUST 27, 2021
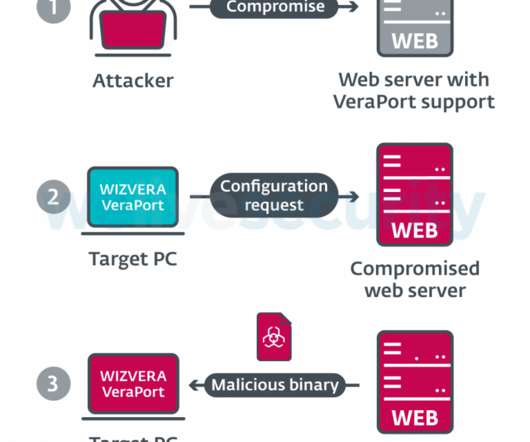
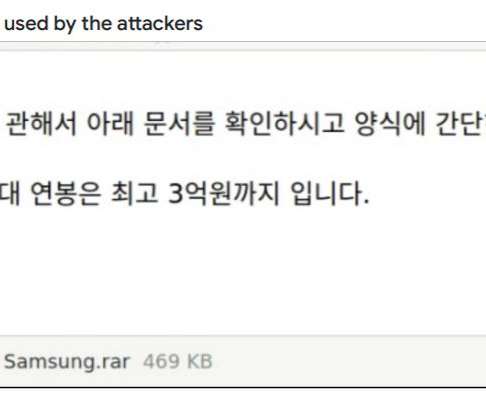
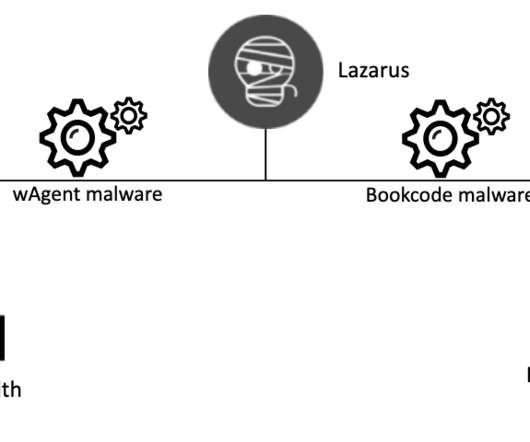
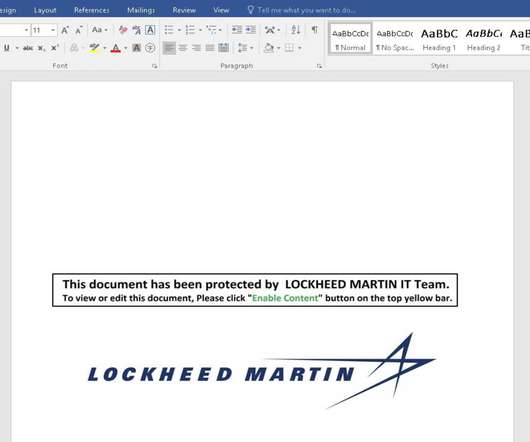
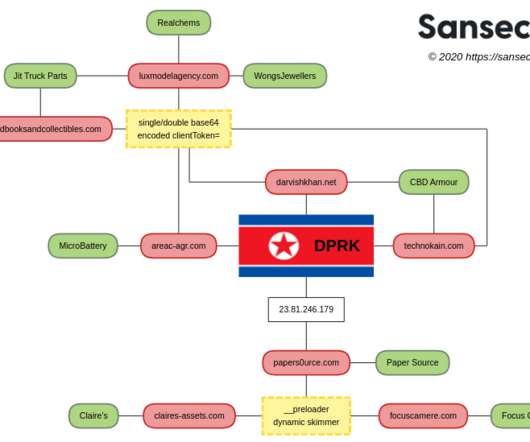
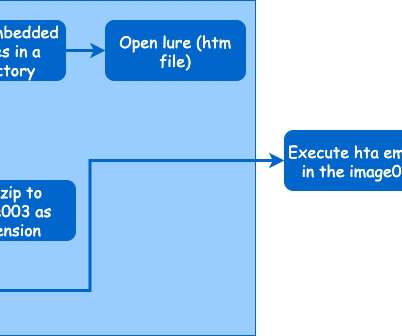
In this week’s post, we take a look at “in-the-wild” phishing attacks and talk about how to protect against a phishing attack and how to counter them. Phishing Attack Examples. Here are two examples of phishing attacks that were carried out. Often malware attacks are multi-functional like our next example.







































Let's personalize your content