Russian spies are attempting to tap transatlantic undersea cables
Security Affairs
MARCH 1, 2020
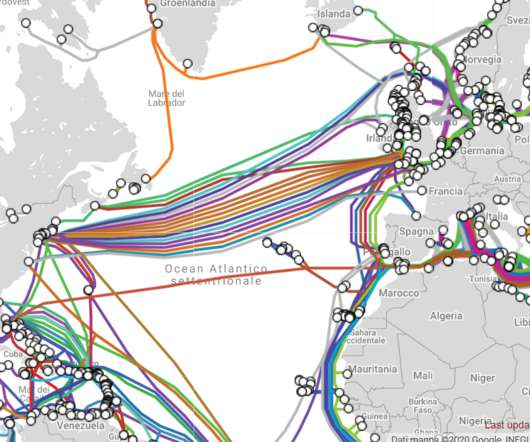
Ireland is a strategic place for intercontinental communications because it represents the place where undersea cables which carry internet traffic connect to Europe. The data collected by the undersea cable would include content from online messages, browsing sessions, VOIP calls, and emails. ” reported The Sunday Times.










Let's personalize your content