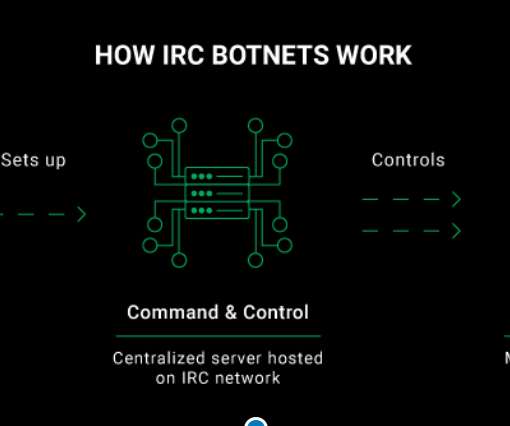
Both Mirai and Hoaxcalls IoT botnets target Symantec Web Gateways
Security Affairs
MAY 19, 2020
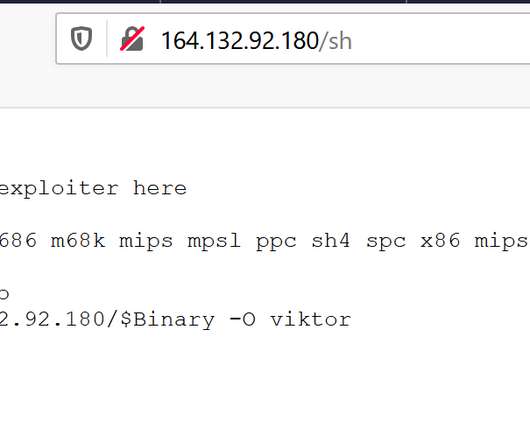
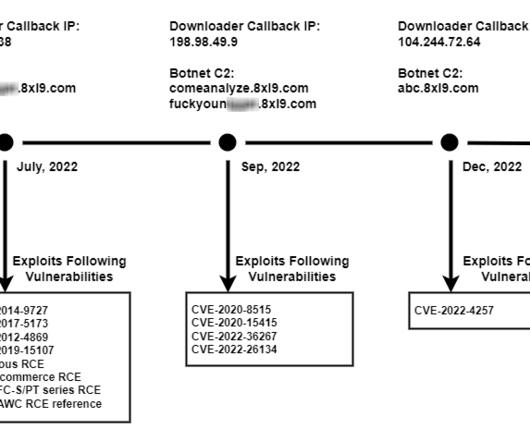
The botnet borrows the code from Tsunami and Gafgyt botnets, it expanded the list of targeted devices and added new distributed denial of service (DDoS) capabilities. In the first week of May, the experts also spotted a Mirai variant using the same exploit, but this samples don’t contain any DDoS capabilities. Pierluigi Paganini.














Let's personalize your content