Security firm accidentally exposed an unprotected database with 5 Billion previously leaked records
Security Affairs
MARCH 22, 2020
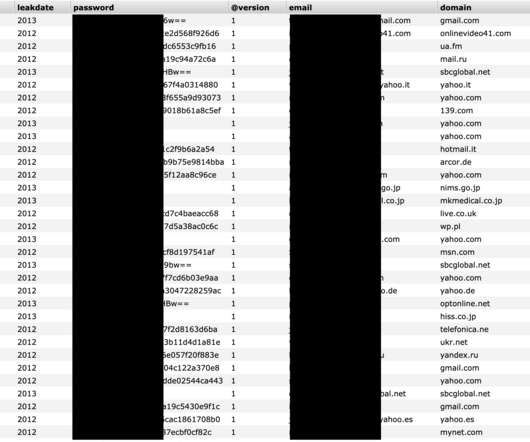
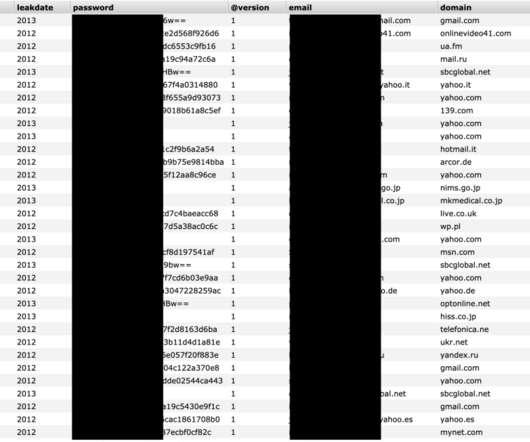
The expert Bob Diachenko has discovered an unsecured Elasticsearch install belonging to a UK security firm that contained 5 billion records of data leaked in previous incidents that took place between 2012 and 2019. ” wrote Security Discovery’s researcher Bob Diachenko.









Let's personalize your content