Understand and Manage Pesky Persistent Threats
McAfee
AUGUST 26, 2020
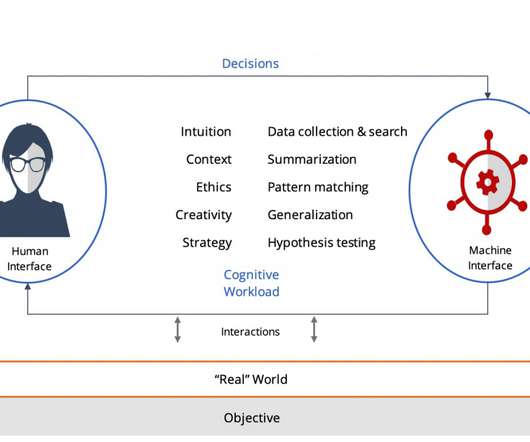
Criminals got clever with social engineering by masquerading the ransomware as a law enforcement agency (perhaps the FBI) and making accusations that illegal files are on the system. Enter MVISION Insights intelligently driving your endpoint security! Fruits of Human Interface and Artificial Intelligence.













Let's personalize your content