Microsoft warns about ongoing PonyFinal ransomware attacks
Security Affairs
MAY 27, 2020
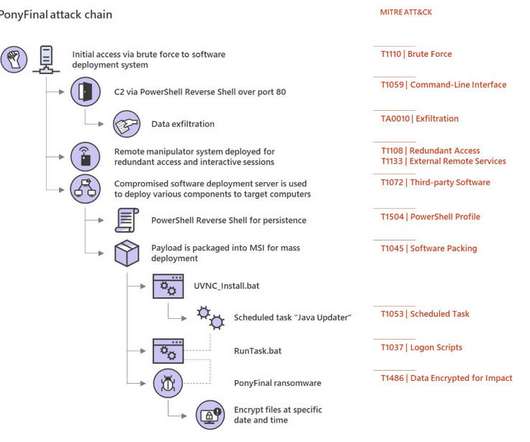
Microsoft is warning organizations to deploy protections against a new strain of PonyFinal ransomware that has been in the wild over the past two months. PonyFinal is Java-based ransomware that is manually distributed by threat actors. PonyFinal is Java-based ransomware that is manually distributed by threat actors.














Let's personalize your content