When Low-Tech Hacks Cause High-Impact Breaches
Krebs on Security
FEBRUARY 26, 2023
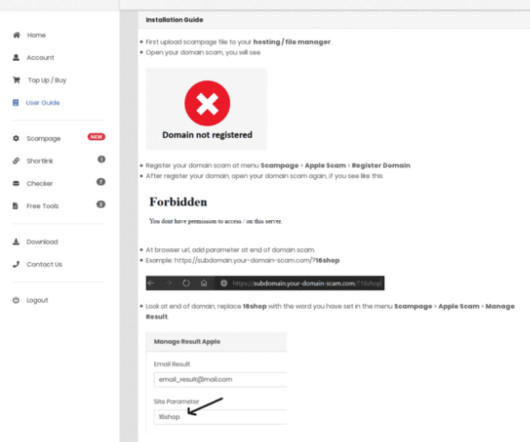
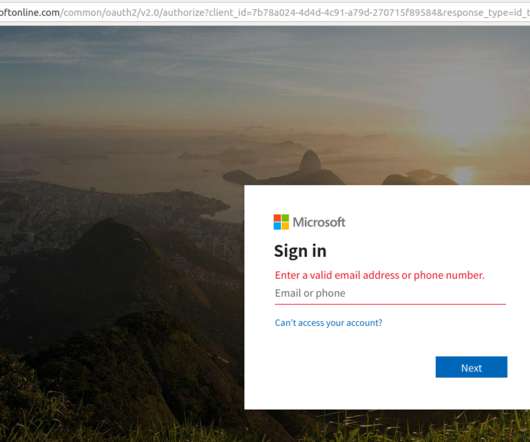
Many companies now require employees to supply a one-time password — such as one sent via SMS or produced by a mobile authenticator app — in addition to their username and password when logging in to company assets online. Thus, the second factor cannot be phished, either over the phone or Internet.











Let's personalize your content