StripedFly: Perennially flying under the radar
SecureList
OCTOBER 25, 2023
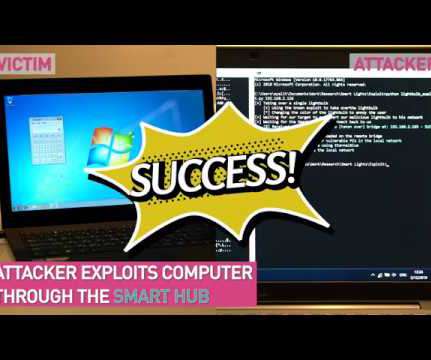
Subsequent analysis revealed earlier instances of suspicious code dating back to 2017. Importantly, our investigation, which considered binary timestamps, indicated that this exploit was created prior to April 2017. It is worth noting that the EternalBlue exploit was publicly disclosed by the Shadow Brokers group on April 14, 2017.











Let's personalize your content