Cybersecurity Incident Response Plans Need Far More Attention
CyberSecurity Insiders
FEBRUARY 25, 2022
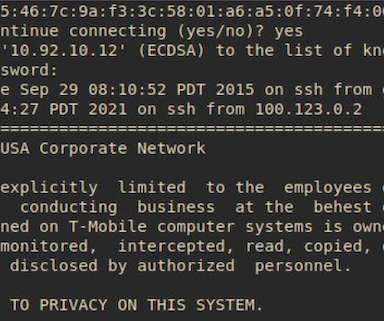
This attack marked its fifth breach since 2018 and, in fact, the company suffered yet another breach – albeit apparently a small one — late in December. Most are spending more on improved cybersecurity technology, but many companies and their employees still aren’t carrying their weight. Detection and analysis.















Let's personalize your content