Duo's Passwordless Authentication is Coming!
Duo's Security Blog
MARCH 30, 2021
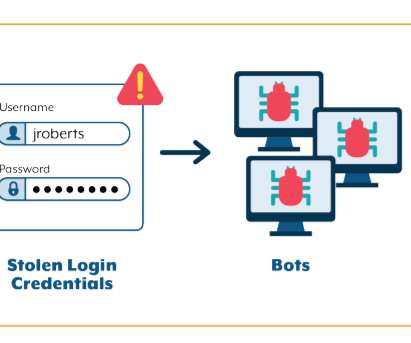
When the number of computers on the internet could be counted with two hands, there was the password. Lo was the first word sent across the internet. What’s Coming I’m excited to share that Cisco is announcing Duo’s passwordless authentication. Workforces are ready for passwordless authentication.












Let's personalize your content