Reverse, Reveal, Recover: Windows Defender Quarantine Forensics
Fox IT
DECEMBER 13, 2023
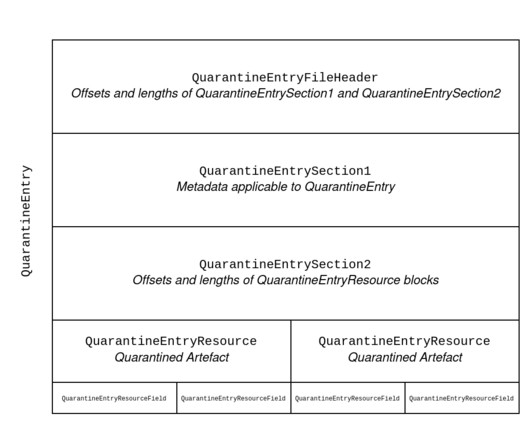
Introduction During incident response engagements we often encounter antivirus applications that have rightfully triggered on malicious software that was deployed by threat actors. Rather than just presenting our results, we’ve structured this blog to also describe the process to how we got there.







Let's personalize your content