“KeyTrap” (CVE-2023-50387) Flaw Leaves DNS Systems Vulnerable, PoC Published
Penetration Testing
FEBRUARY 19, 2024
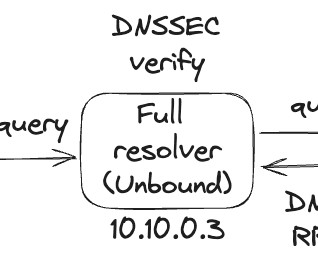
A proof-of-concept (PoC) was disclosed for a severe design flaw (CVE-2023-50387) in Domain Name System Security Extensions (DNSSEC), leaving DNS infrastructures vulnerable to widespread denial-of-service (DoS) attacks.



















Let's personalize your content