Canadian authorities arrested alleged Snowflake hacker
Security Affairs
NOVEMBER 5, 2024
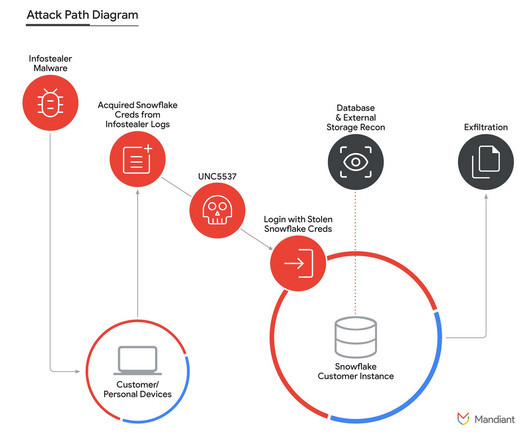
Canadian law enforcement agencies arrested a suspect, Alexander “Connor” Moucka (aka Judische and Waifu), who is accused of being responsible for a series of attacks relying on information stolen from the cloud data warehousing platform Snowflake earlier this year. Charges remain undisclosed.





















Let's personalize your content