Simplify Network Security with Cisco Secure Firewall-as-a-service (FWaaS) on AWS
Cisco Security
NOVEMBER 29, 2021
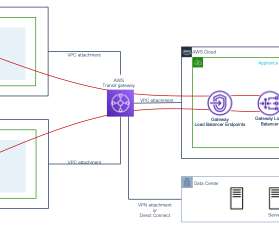
According to Gartner, by 2025, 30% of new deployments of distributed branch-office firewalls will switch to firewall-as-a-service, up from less than 10% in 2021. Other benefits include: Simplified security architecture – Provisioning of firewalls and control plane infrastructure are managed by Cisco, saving time and accelerating value.














Let's personalize your content