SOC 2025: Detection/Analytics
Security Boulevard
MARCH 10, 2022
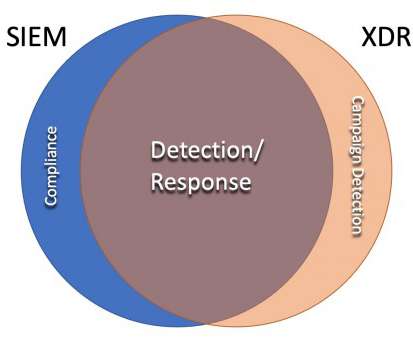
Once you have internal and external data collected and aggregated, you analyze the data to identify the attacks. Attackers are more organized and proficient — once they have a foothold within a victim’s network, they perform extensive reconnaissance to find and destroy backups, increasing pressure to pay the ransom.









Let's personalize your content