Inside Ireland’s Public Healthcare Ransomware Scare
Krebs on Security
DECEMBER 13, 2021
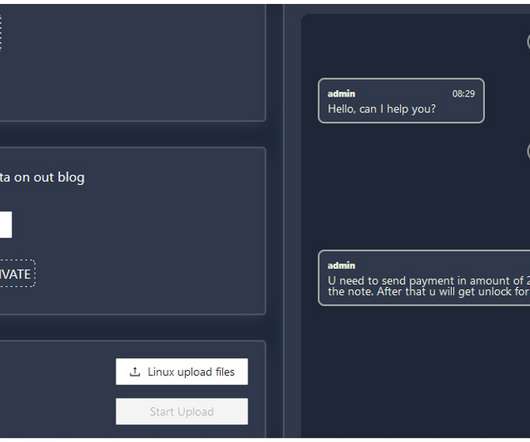
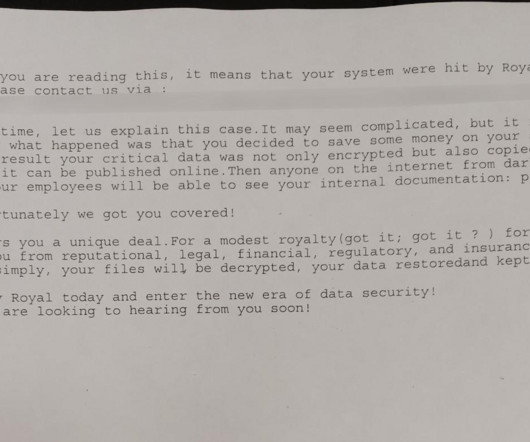
31, 2021, the HSE’s antivirus software detected the execution of two software tools commonly used by ransomware groups — Cobalt Strike and Mimikatz — on the Patient Zero Workstation. But the antivirus software was set to monitor mode, so it did not block the malicious commands.”






















Let's personalize your content