How to Comply with GDPR, PIPL, and CCPA
eSecurity Planet
DECEMBER 22, 2021
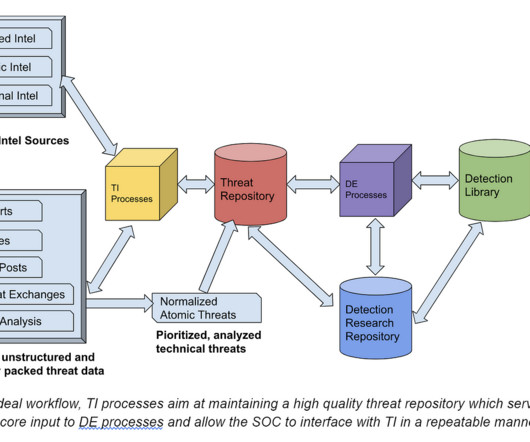
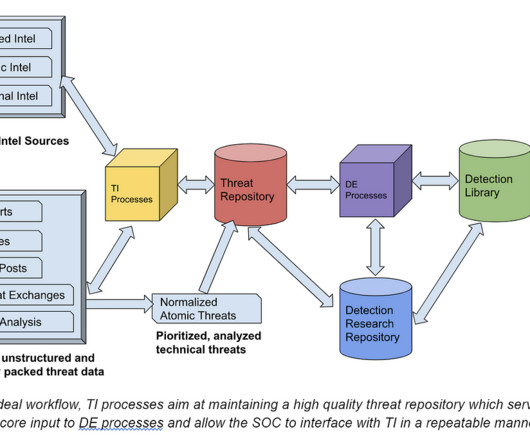
Also Read: China’s Data Privacy Law Poses Challenge for International Companies. Organizations need to understand all of the data they store and collect as well as where they’re storing it. Categories for all of your organization’s data: Not every piece of information will be relevant to CCPA and require the same level of security.










Let's personalize your content