Russian APT Nomadic Octopus hacked Tajikistani carrier
Security Affairs
MAY 1, 2023
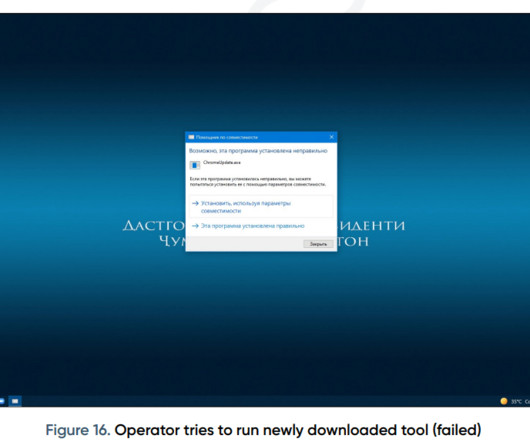
Russian APT group Nomadic Octopus hacked a Tajikistani carrier to spy on government officials and public service infrastructures. ” reads the report published by cyber threat intelligence firm Prodaft.

















Let's personalize your content