New variant for Mac Malware XCSSET compiled for M1 Chips
Security Affairs
MARCH 13, 2021
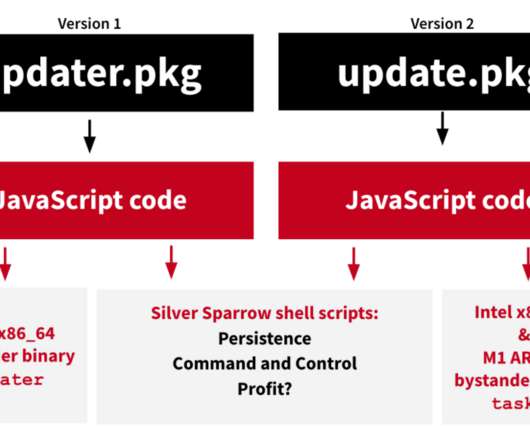
For example, a sample with the MD5 hash sum 914e49921c19fffd7443deee6ee161a4 contains two architectures: x86_64 and ARM64.” “The first one corresponds to previous-generation, Intel-based Mac computers, but the second one is compiled for ARM64 architecture, which means that it can run on computers with the new Apple M1 chip.”











Let's personalize your content