Breach Exposes Users of Microleaves Proxy Service
Krebs on Security
JULY 28, 2022
Launched in 2013, Microleaves is a service that allows customers to route their Internet traffic through PCs in virtually any country or city around the globe. Microleaves works by changing each customer’s Internet Protocol (IP) address every five to ten minutes. Which hints at a possible BOTNET. “Online[.]io



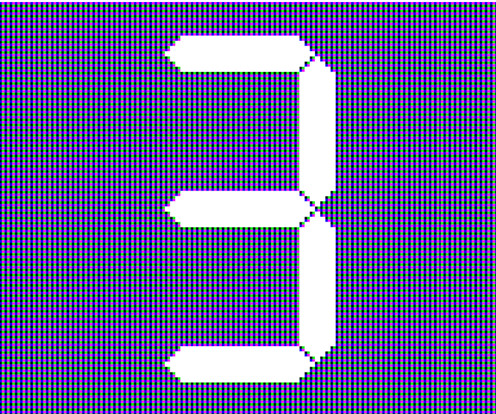










Let's personalize your content