3 crucial security steps people should do, but don't
Malwarebytes
OCTOBER 17, 2023
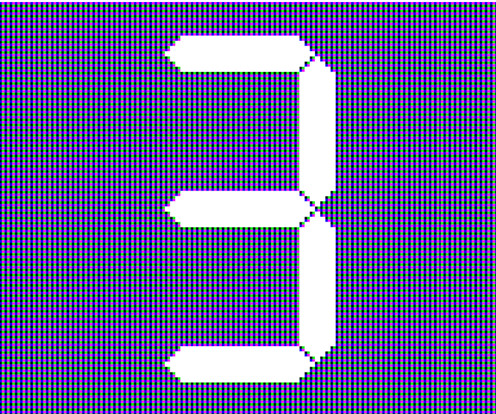
Just 24 percent of people use multi-factor authentication. Just 15 percent of people use a password manager. Just 35 percent of people have unique passwords for most or all of their accounts. Instead, it demands an increasing number of accounts and passwords to manage for each person.











Let's personalize your content