Apple removed the popular app Adware Doctor because steals user browsing history
Security Affairs
SEPTEMBER 8, 2018
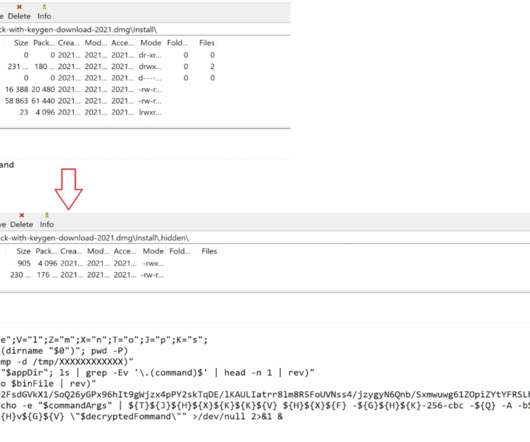
Apple has removed one of the most popular anti-malware app called Adware Doctor:Anti Malware &Ad from the official macOS App Store. Adware Doctor the top paid utility in the official Mac App Store, it has a good reputation with thousands of reviews and a 4.8 Adware Doctor is stealing your privacy. star rating.











Let's personalize your content