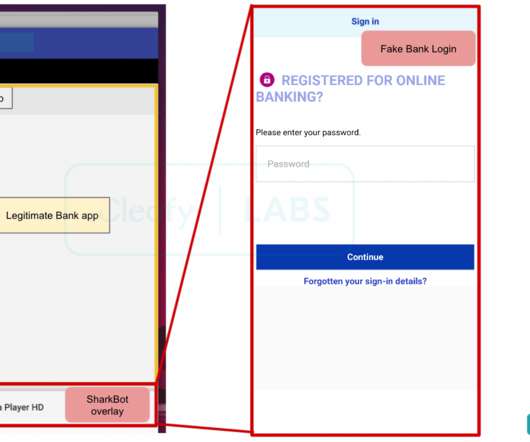
SharkBot, a new Android Trojan targets banks in Europe
Security Affairs
NOVEMBER 15, 2021
The trojan allows to hijack users’ mobile devices and steal funds from online banking and cryptocurrency accounts. Once the banking Trojan is installed on the victim’s device, threat actors can steal sensitive banking information through the abuse of Accessibility Services (i.e. ” concludes the report.














Let's personalize your content