Information risk and security for professional services
Notice Bored
APRIL 20, 2022
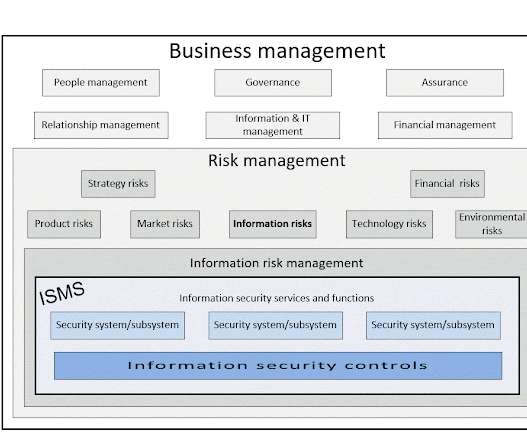
When you acquire or provide professional services, how do you address the associated information risks? Professional services are information-centric: information is the work product , the purpose, the key deliverable. Guess whose interests they are most likely to protect!










Let's personalize your content