Alleged Boss of ‘Scattered Spider’ Hacking Group Arrested
Krebs on Security
JUNE 15, 2024
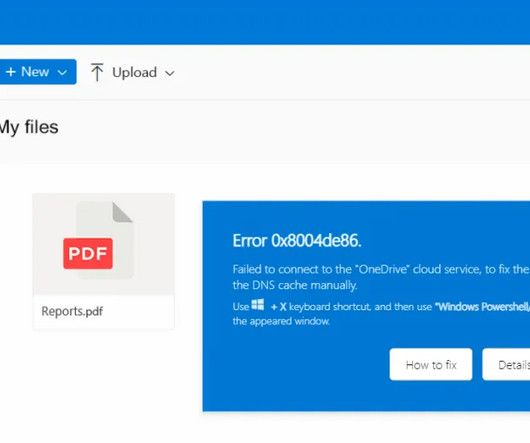
A 22-year-old man from the United Kingdom arrested this week in Spain is allegedly the ringleader of Scattered Spider , a cybercrime group suspected of hacking into Twilio , LastPass , DoorDash , Mailchimp , and nearly 130 other organizations over the past two years. man arrested was a SIM-swapper who went by the alias “ Tyler.”











































Let's personalize your content