The evolution of ransomware in 2019: attackers think bigger, go deeper and grow more advanced
Security Affairs
MAY 27, 2020
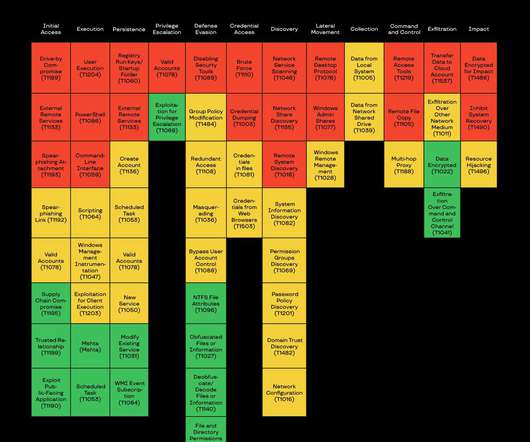
The findings come as highlights of Group-IB whitepaper titled “ Ransomware Uncovered: Attackers’ Latest Methods ,” closely examining the evolution of the ransomware operators’ strategies over the past year, issued today. More recommendations can be found in the relevant section of the whitepaper. . Big Game Hunting. How it all began.












Let's personalize your content