Penetration Testing Remote Workers
SecureWorld News
JUNE 28, 2020
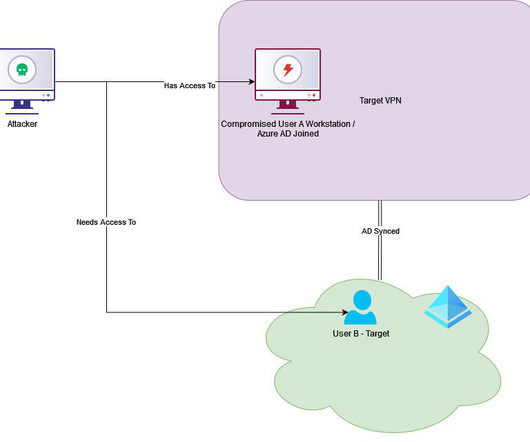
With many organizations now planning their annual penetration tests ("pentest" for short), a change is needed in order to accommodate remote workers. It also begs what are you allowed to test versus what is now considered taboo considering end-users may be operating with their own personal equipment?
















Let's personalize your content