5 ways to strengthen healthcare cybersecurity
Webroot
APRIL 5, 2024
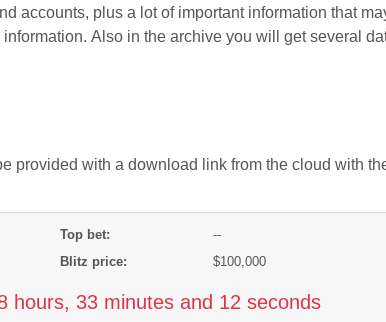
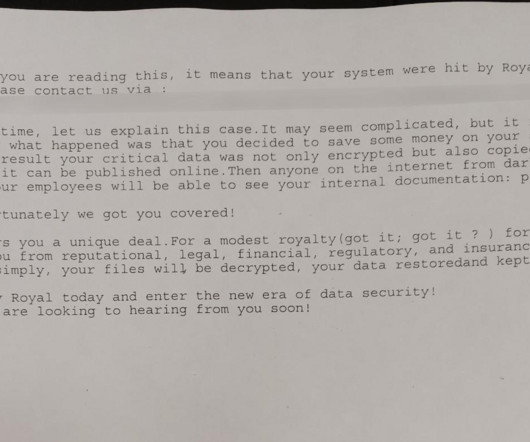
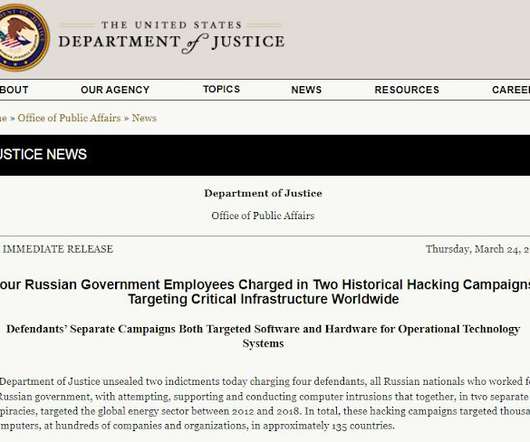
Ransomware attacks are targeting healthcare organizations more frequently. Why healthcare needs better cybersecurity Healthcare organizations are especially vulnerable to data breaches because of how much data they hold. On average, the cost of a healthcare data breach globally is $10.93





































Let's personalize your content