How To Make Your Website Safer For Users And Websites That Hold Business Data And Information
IT Security Guru
MAY 12, 2024
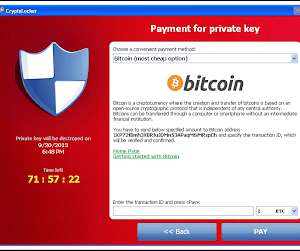
Employ Firewalls Firewalls act as a barrier between your website and potential attackers, especially if you work in industries that carry a lot of sensitive data including large corporations, insurance firms, medical practices and companies that offer bad credit loans. Regular Backups Regularly back up your website and business data.




























Let's personalize your content