Demo: Your data has been encrypted! Stopping ransomware attacks with Malwarebytes EDR
Malwarebytes
JULY 26, 2022
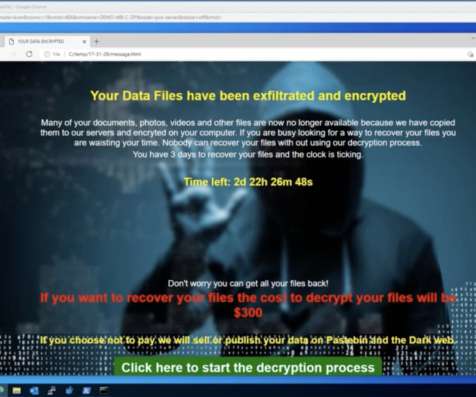
Part 1: Your data has been encrypted! Part 1: Your data has been encrypted! As you can see, our files have in fact been encrypted by the ransomware across multiple directories with the “ encrypt ” extension. encrypted versions of the same file. . Watch the webinar !















Let's personalize your content