No SOCKS, No Shoes, No Malware Proxy Services!
Krebs on Security
AUGUST 2, 2022
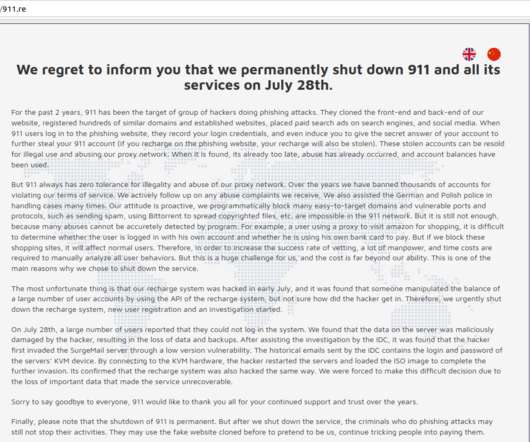
Compounding the problem, several remaining malware-based proxy services have chosen to block new registrations to avoid swamping their networks with a sudden influx of customers. re abruptly announced it was permanently closing after a cybersecurity breach allowed unknown intruders to trash its servers and delete customer data and backups.











Let's personalize your content