Russian Cybercrime group is exploiting Zerologon flaw, Microsoft warns
Security Affairs
OCTOBER 10, 2020
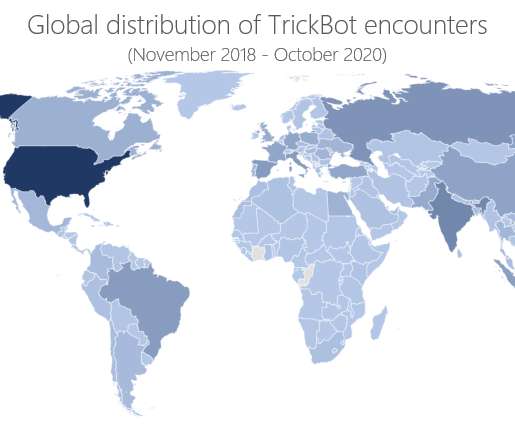
TA505 hacking group has been active since 2014 focusing on Retail and banking sectors. The TA505 group was involved in campaigns aimed at distributing the Dridex banking Trojan, along with Locky , BitPaymer , Philadelphia , GlobeImposter , and Jaff ransomware families. states Microsoft. We strongly recommend patching.
















Let's personalize your content