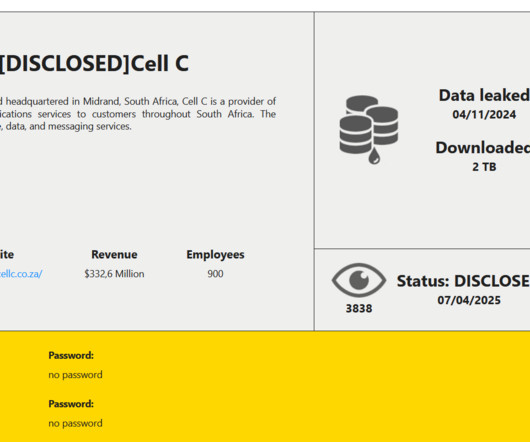
South African telecom provider Cell C disclosed a data breach following a cyberattack
Security Affairs
APRIL 13, 2025
The ransomware group has since leaked the stolen data on its dark web leak site. The gang claimed the theft of 2 TB of data. Compromised data includes full names, contact details, ID numbers, banking information, drivers license numbers, medical records and passport details. ” states the company.














Let's personalize your content