LockFile Ransomware uses a new intermittent encryption technique
Security Affairs
AUGUST 31, 2021
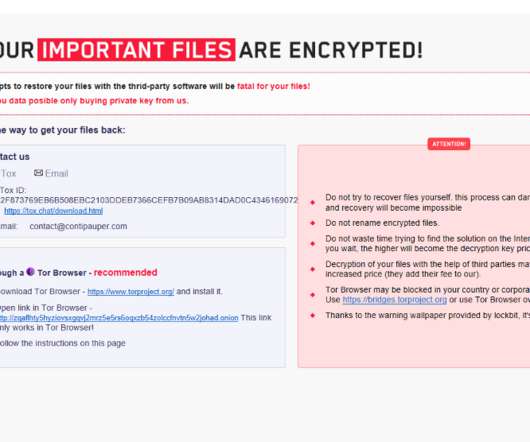
Recently emerged LockFile ransomware family LockFile leverages a novel technique called intermittent encryption to speed up encryption. LockFile ransomware gang started its operations last month, recently it was spotted targeting Microsoft Exchange servers using the recently disclosed ProxyShell vulnerabilities.













Let's personalize your content