Breaking the Zeppelin Ransomware Encryption Scheme
Schneier on Security
NOVEMBER 21, 2022
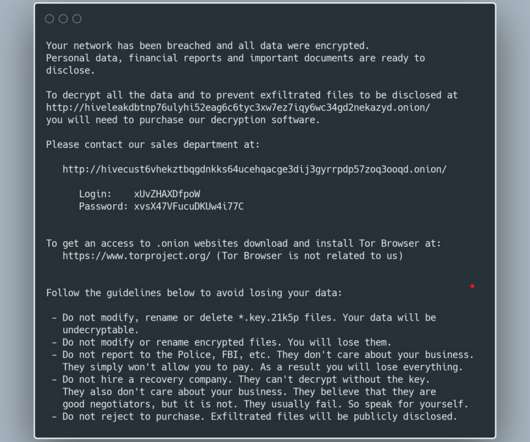
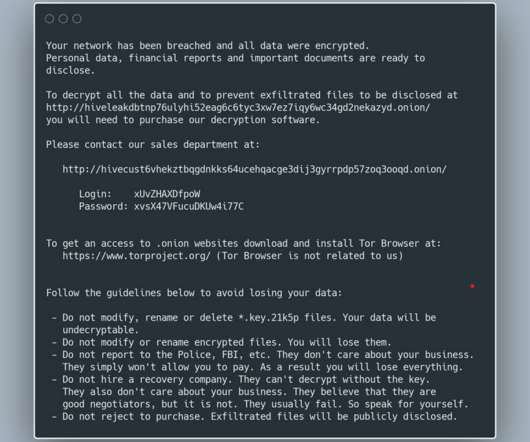
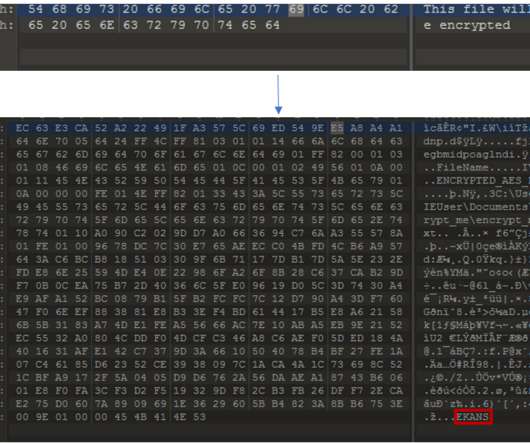
“If we can recover the RSA-512 Public Key from the registry, we can crack it and get the 256-bit AES Key that encrypts the files! . “If we can recover the RSA-512 Public Key from the registry, we can crack it and get the 256-bit AES Key that encrypts the files!” ” they wrote. Technical details.










































Let's personalize your content