Malware Training Sets: FollowUP
Security Affairs
MAY 14, 2019
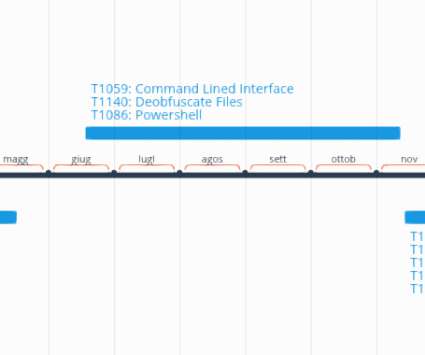
The popular expert Marco Ramilli provided a follow up to its Malware classification activity by adding a scripting section which would be useful for several purposes. On 2016 I was working hard to find a way to classify Malware families through artificial intelligence (machine learning).


















Let's personalize your content